90.150.504: System Access & Traffic Summary
The “90.150.504: System Access & Traffic Summary” report systematically dissects user engagement metrics, revealing access patterns shaped by demographic and geographic factors. It meticulously highlights interaction trends, which are critical for optimizing system performance and enhancing user experience. Moreover, the report underscores the necessity of stringent security protocols to safeguard user confidence. Understanding these dynamics is essential to addressing vulnerabilities and improving overall operational effectiveness. What insights emerge from these findings?
Key Metrics and Trends in System Access
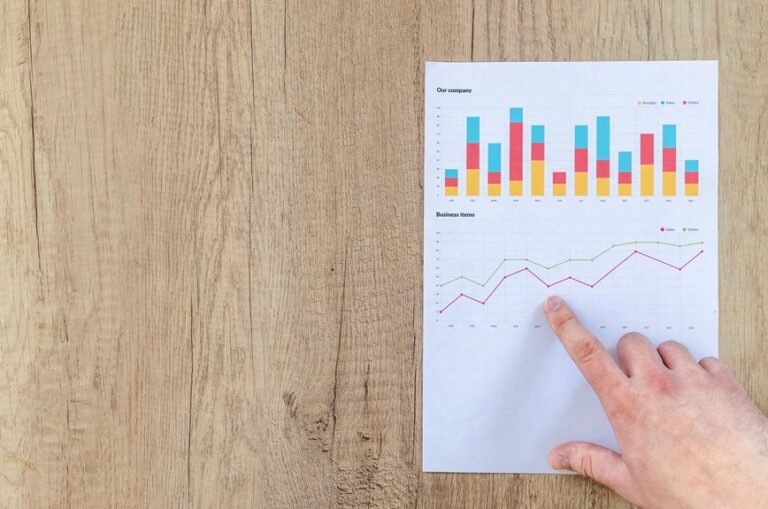
The analysis of key metrics and trends in system access reveals significant insights into user engagement and operational efficiency.
Evaluating user demographics indicates varied access frequency, highlighting distinct patterns among different age groups and locations.
Understanding these trends enables organizations to optimize system design, enhance user experience, and ultimately align operational strategies with the diverse needs and preferences of their user base, fostering greater autonomy.
Analyzing User Interaction Patterns
User interaction patterns provide valuable insights into how individuals engage with systems, reflecting their behaviors and preferences.
By analyzing metrics such as usage frequency, organizations can discern levels of user engagement. This data enables a deeper understanding of user habits, facilitating enhancements that cater to individual needs.
Ultimately, such insights empower users, fostering an environment that promotes autonomy and satisfaction in system interactions.
Identifying Vulnerabilities and Security Enhancements
Identifying vulnerabilities within a system is crucial for maintaining robust security measures.
Conducting a thorough vulnerability assessment enables organizations to pinpoint weaknesses in existing security protocols. By systematically evaluating potential risks, organizations can implement targeted enhancements that fortify defenses.
This proactive approach not only mitigates threats but also empowers users, fostering a secure environment conducive to freedom and innovation within digital spaces.
Conclusion
In conclusion, the “90.150.504: System Access & Traffic Summary” report offers invaluable insights into user engagement and security dynamics. By meticulously analyzing access metrics and interaction patterns, it provides a roadmap for optimizing user experiences and fortifying system defenses. The critical identification of vulnerabilities ensures that users navigate the platform with the confidence of a knight in shining armor. Ultimately, this report serves as a cornerstone for enhancing operational efficiency and cultivating a secure digital environment.